How do I set up AD Sync?
If your organization uses Azure Active Directory (AD), you can configure an application in the Azure portal that will allow Hook Security to sync with the directory
You will create an application registration in your AD, assign the proper API permissions, then share the application credentials via SendSafely to Hook Security. After doing so, Hook Security will be able to connect to your AD and import your AD's groups and users.
Registering the Application
To start, navigate to the Azure portal and sign in. Once signed in, click the hamburger menu in the top-left of the portal and click Azure Active Directory. After navigating to Azure Active Directory, Click App Registrations in the navigation menu on the left-hand side.
Once in the App Registrations window, click the "New registration" button, located on the top of the page.
This will open the application registration wizard. Complete the following steps:
- Give the application a name.
- Under the Supported account types section, select the "Accounts in this organization directory only" option.
- Click the "Register" button on the bottom left-hand side of the wizard.
NOTE: A Redirect URI is not required.
Assigning Permissions
Now the application has been created and you will be redirected to the application overview. Note the Application (client) ID and Directory (tenant) ID. Hook Security, Inc will need both, along with a secret, in order to connect to the directory. Before you enter the App ID and Directory ID into Hook Security, Inc, the application needs API permissions. Click the "View API permissions" button under the Call APIs section, or the "API permissions" link in the navigation menu on the left-hand side.
After navigating to the API Permissions page, complete the following steps:
- Click the "Add a permission" button, located above the "Configured permissions" table.
- You will then need to select an API, select Microsoft Graph.
- Select Delegated permissions.
- Click the respective checkboxes for each permission below:
- Directory.Read.All
- Group.Read.All
- GroupMember.Read.All
- profile
- User.Read
- User.Read.All
- User.ReadBasic.All
- Click "Add permissions", located at the bottom of the Request API permissions form, to add the permissions to the application.
- Click the "Add a permission" button, located above the "Configured permissions" table.
- You will then need to select an API, select Microsoft Graph.
- Select Application permissions.
- Click the respective checkboxes for each permission below:
- Directory.Read.All
- Group.Read.All
- GroupMember.Read.All
- User.Read.All
- Click "Add permissions", located at the bottom of the Request API permissions form, to add the permissions to the application.
- After being redirected back to the application's API permissions page, click the "Grant admin consent" button on the application's API permissions page.
NOTE: Administrator consent will be required to grant the selected permissions to the application. The minimum admin privileges required to grant consent are Application privileges.
You will be asked to verify, click "Yes" to continue. If the permissions are granted successfully, is displayed in the 'Status' column for the respective permissions. Once you are done adding permissions, the API permissions page should look something like this:
Credentials
Next, the credentials needed for Hook Security, Inc to connect will have to be collected. Hook Security, Inc requires three distinct keys or ids in order to connect to your AD:
- Application (client) ID
- Directory (tenant) ID
- Client secret
IDs
The Application ID and Directory ID are displayed in the Overview tab of the application page. Click the Overview link in the navigation menu on the left-hand side.
The Application ID and the Directory ID will be displayed at the top of the page below the application's display name.
Client Secret
Click the Certificates & secrets link in the navigation menu on the left-hand side of the Azure portal.
Under the Client secrets tab, click the "New client secret" button.
You will be prompted to give the secret a description and select an expiry date.
NOTE: If you choose to allow the secret to expire, after expiration another secret will need to be generated and the integration will need to be reconfigured.
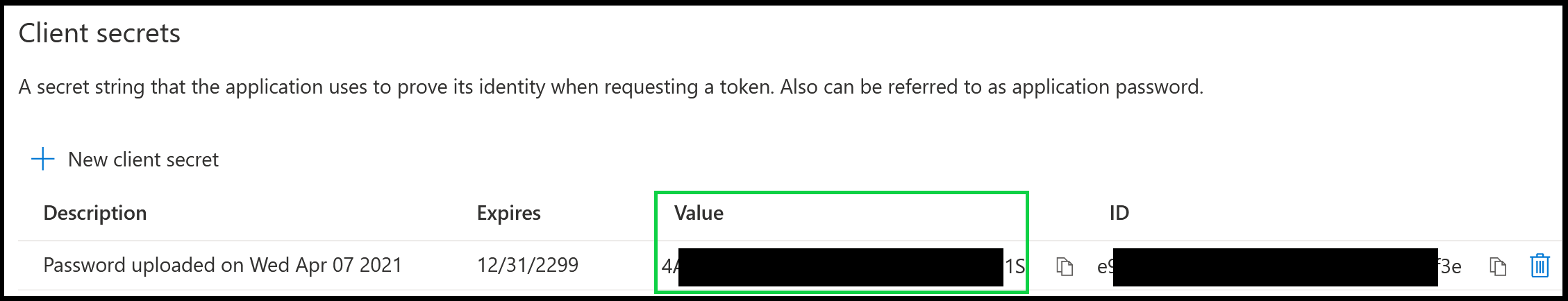
After the secret is generated, you will want to save/copy the secret value (circled in green in the below screenshot). If you navigate away from the page, the secret will be obscured and you will not be able to copy the secret value to the clipboard. If you do not save the secret or it is obscured, you can always generate another one. Keep in mind that if the secret entered in Hook Security, Inc is deleted from the application registration or expires the integration will have to be reconfigured in Hook Security, Inc.
Now that you have configured the application and have the IDs and secret at hand, your Azure AD can be integrated with Hook Security, Inc.
Integrating with Hook Security, Inc
To integrate your Azure AD with Hook Security, Inc, log in to the Hook Security, Inc portal and navigate to Administration > Integration Store.
Click the Setup button on Azure AD's respective card. This will open the setup form for Azure AD. If you wish for the sync to occur immediately after saving the configuration, set the 'Active' switch to 'Yes'. Click "Test" to connect Hook Security, Inc to your AD. If a connection is successful, your AD's groups will appear in the select box. Select the groups you want to sync with Hook Security, Inc then click the "Save" button.
NOTE: If you are syncing other groups using Azure and they are not located in this integration, setting the integration sync to active will cause the other groups to become inactive. You can also sync Azure groups at the group level from the Edit Group page. If an Azure group is synced via this method, but does not appear in the Edit Configuration pop-up for the integration, then setting the integration to active will cause the group to become inactive.
If there are more than 250 groups in the directory, then you will choose the groups using a search box, as shown below.
If the Active option was set to Yes, then the group(s) will be scheduled to sync in. The Azure card will say "Sync Queued". When the sync is finished, an integration_sync_finished email will be sent to the Account Manager Email (set on the Notifications tab on the Account Settings page).
When the sync completes, it will say "Synced".
If you did not set the integration to active, you can sync later by selecting "Run Sync" from the drop-down menu located at the bottom right-hand side of the integration's card. Then, the group will be scheduled for a sync. When the sync is finished, an integration_sync_finished email will be sent to the Account Manager Email (set on the Notifications tab on the Account Settings page). You can view the results of the last time the integration was synced by clicking on "Last Sync Logs" in the drop-down.