How do you set up SSO Pingone?
This article instructs the necessary steps to set up SAML PingOne.
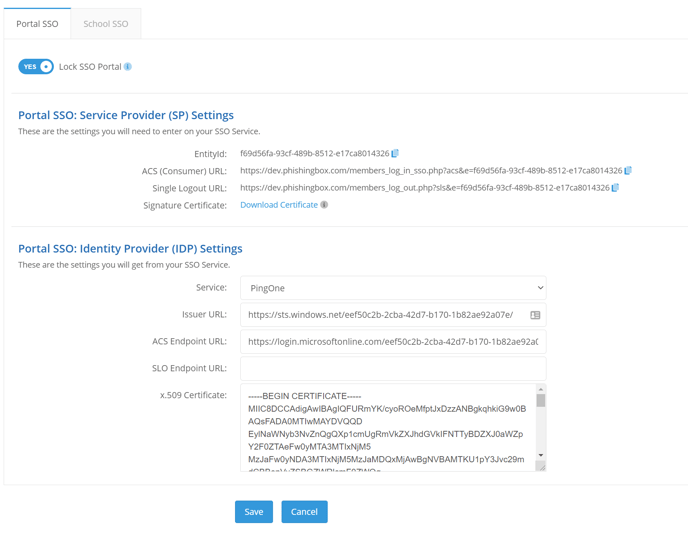
You can set up SSO on the SSO Settings page for both the Portal and the School, but you will need to create two separate applications on your IDP (this is due to needing to use different URLs). The top section are Portal settings that you will paste into your IDP and the bottom section are settings that you will get from your IDP. To navigate to the Portal SSO Settings for PingOne, go to Administration > Settings > SSO Settings.
NOTE: If a user is provided access to the phishing portal via your organization's SSO IDP and does not already have an account in the phishing portal (in Administration>Manage Portal Users), an account will automatically be created with a role of "Admin" when the user accesses the phishing portal via SSO.
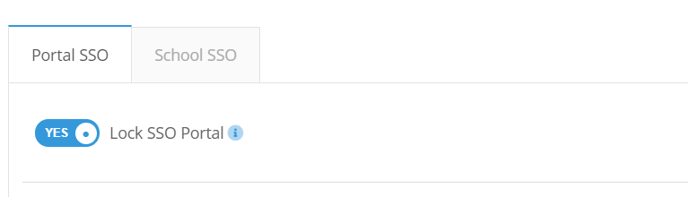
SSO Lock
If enabled, administrators can log in to the portal via SSO only. If the SSO configuration fails and administrators can no longer log in, you will have to contact support in order to disable this feature.
Select PingOne from the Service drop-down
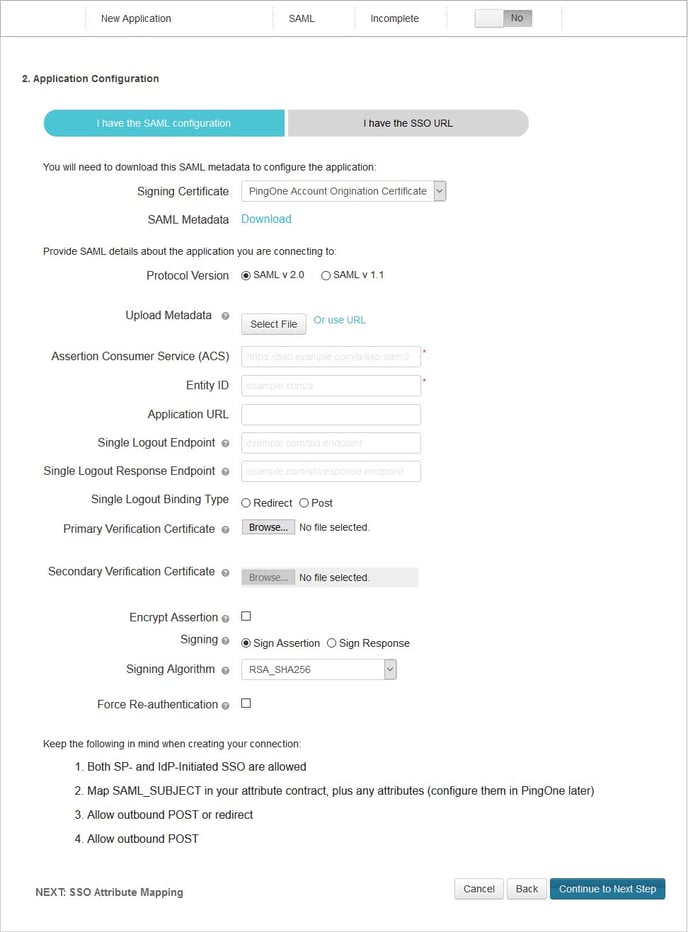
From the PingOne Admin portal, go to the Applications section and add a "New SAML Application."
Step 1: Application Details
Give your new application a name, category, and upload an icon of your choice.
Step 2: Application Configuration
Portal SP Settings you plugin into your IDP:
- ACS (Consumer) URL -> Assertion Consumer Service (ACS)
- EntityId -> Entity ID
- Your Whitelabeled URL -> Application URL (Note: Be sure to add "/index.php" to the end of your whitelabled URL. For example, if your whitelabled URL is "https://yourcompanyschool.testingcenter.net", you'd want to use https://yourcompanyschool.testingcenter.net/index.php as the Application URL.)
- Single Logout URL -> Single Logout Endpoint
Your IDP settings you plugin into Portal SP:
Download the SAML Metadata XML to find these settings.
Use the following settings in the SAML Metadata XML file to fill in the corresponding settings in the portal;
- entityID -> Issuer URL
- X509Certificate -> x.509 Certificate
- SingleLogoutService -> SLO Endpoint URL
- SingleSignOnService -> ACS Endpoint URL
<?xml version="1.0"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="g7r1YVie-iqysV037OuX9rIpUDO" entityID="https://pingone.com/idp/yourcompany">
<md:IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx== </ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx== </ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sso.connect.pingidentity.com/sso/SLO.saml2"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sso.connect.pingidentity.com/sso/SLO.saml2"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sso.connect.pingidentity.com/sso/idp/SSO.saml2?idpid=XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" Name="PingOne.AuthenticatingAuthority" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
<saml:Attribute xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" Name="PingOne.idpid" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/>
</md:IDPSSODescriptor>
</md:EntityDescriptor>
Step 3: SSO Attribute Mapping
You can skip this step.
Step 4: Group Access
Select which of your groups you want to be able to use this application. When assigning a user to the phishing portal, an admin will be created.
Step 5: Review Setup
Click Finish.
Note: A sign in URL can be obtained from the users IDP, usually it will be a URL with query parameters.