How do I integrate with Splunk SIEM?
The Splunk integration allows the Hook Security, Inc platform to push events to your Splunk SIEM tenant.
Follow the steps below to push events from Hook Security, Inc to Splunk.
- Create an HTTP Event Collector
- Integration Store
Create an HTTP Event Collector
First, create an HTTP Event Collector in your Splunk tenant. For instructions, see Splunk Docs.
Leave the 'Enable indexer acknowledgement' checkbox unchecked.
Integration Store
Log into Hook Security, Inc. Navigate to Administration > Integration Store.
In the Integration Store, click the 'Setup' button located on Splunk card.

Fill out the Splunk form. Provide your splunk domain/host and the token for the HTTP Event Collector created in step one. Set the 'Active' switch to yes to immediately activate the integration upon save.
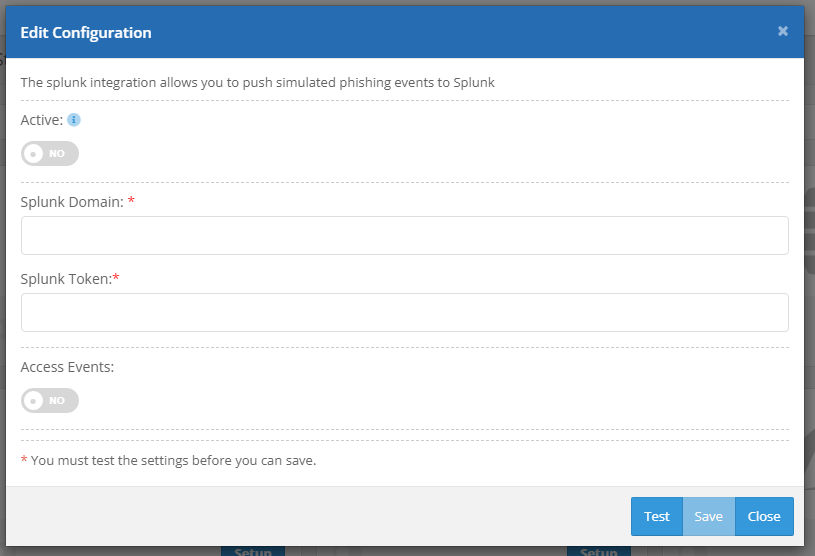
Click the 'Test' button to test the connection. If successful, this will log a `test_connection` event.
If the test is successful, enable the types of events you'd like to log then click 'Save' to finish.
NOTE: If the 'Active' switch is not set to yes upon save, you will have to activate the integration later to push events.
Events
- Access Events: If enabled, will push `access`, `access_denied`, and `logout` events to Splunk.
NOTE: More events will be available in the future. Check Hook Security, Inc change logs for updates.