How do I safelist by IP Address in Exchange 2013, 2016, or Office 365?
The following details the process of safelisting our simulated phishing IPs on your Exchange 2013, 2016, or Office 365 platforms.
Mail filters will sometimes block the emails originating from our IP, but there is a way to resolve this issue with safelisting. Safelisting allows for phishing emails sent from PhishingBox's IP to bypass any mail filters, junk, or spam and clutter folders. We recommend to safelist by IP if possible (for example if you are using a cloud security system). When safelisting by IP is not applicable, safelisting by header is an effective way to make sure that phishing emails are delivered. Below we will show you how to set up an IP allow list as well as rules for Spam and Clutter and the Junk folder.
In addition to safelisting, we strongly recommend that you also set up a connector in Office 365. This will prevent Portal emails from being blocked due to Microsoft greylisting.
f you are using Exchange Server 2010, Exchange Server 2013, Exchange Server 2016, or Exchange Server 2019, you can set up an IP allow list using the command line. See these instructions for more information.
If you do not wish to use the command line, follow the instructions below to set up an IP allow list using the exchange GUI.
- Log into your mail server admin portal and click Admin.
- Click on Exchange.
- Click on connection filter (beneath protection heading).
- Click on connection filter in the protection section, then click the

- Click on connection filtering.
- Under the IP Allow list, click the
 to add an IP address.
to add an IP address. - On the Add allowed IP address prompt, add our IP addresses one at a time.
- Click Save. After setting up an IP allow list, you will want to set up a mail flow rule to permit our mail to bypass spam filtering and the clutter folder.
Completed Connection Filtering
Sending IPs: 64.191.166.196 (US) or 64.238.34.10 (EU).
We also recommend safelisting the IP addresses below for improved deliverability:-
64.191.166.196
64.191.166.197
198.61.254.6
54.80.160.189
64.191.166.198
54.88.246.212
54.240.70.101
54.240.70.102Bypassing Clutter and Spam Filtering
To ensure Portal messages will bypass your Clutter folder as well as spam filtering in Microsoft's EOP, follow the steps below.
- Go to Admin > Mail > mail flow > rules
- Click the
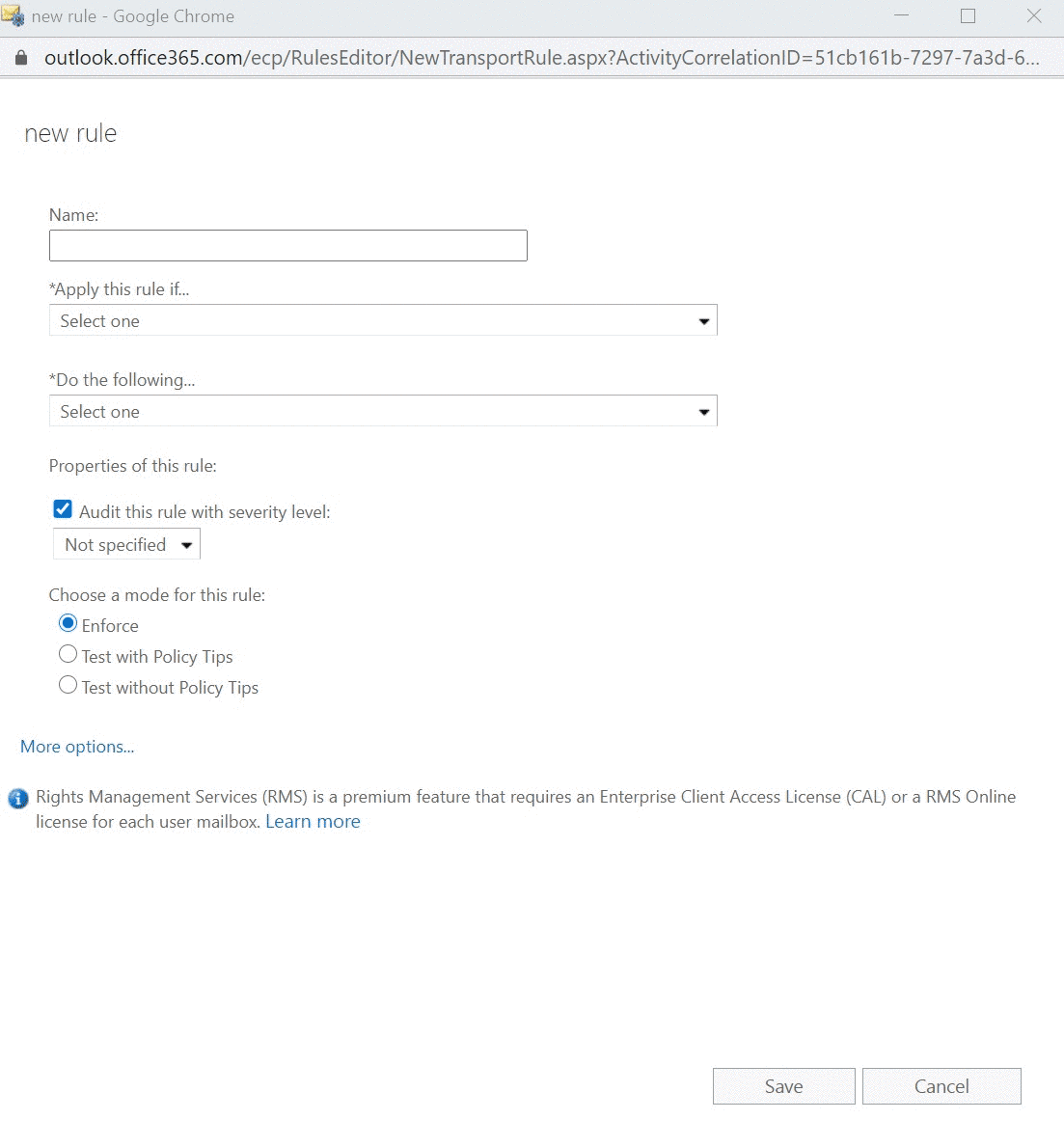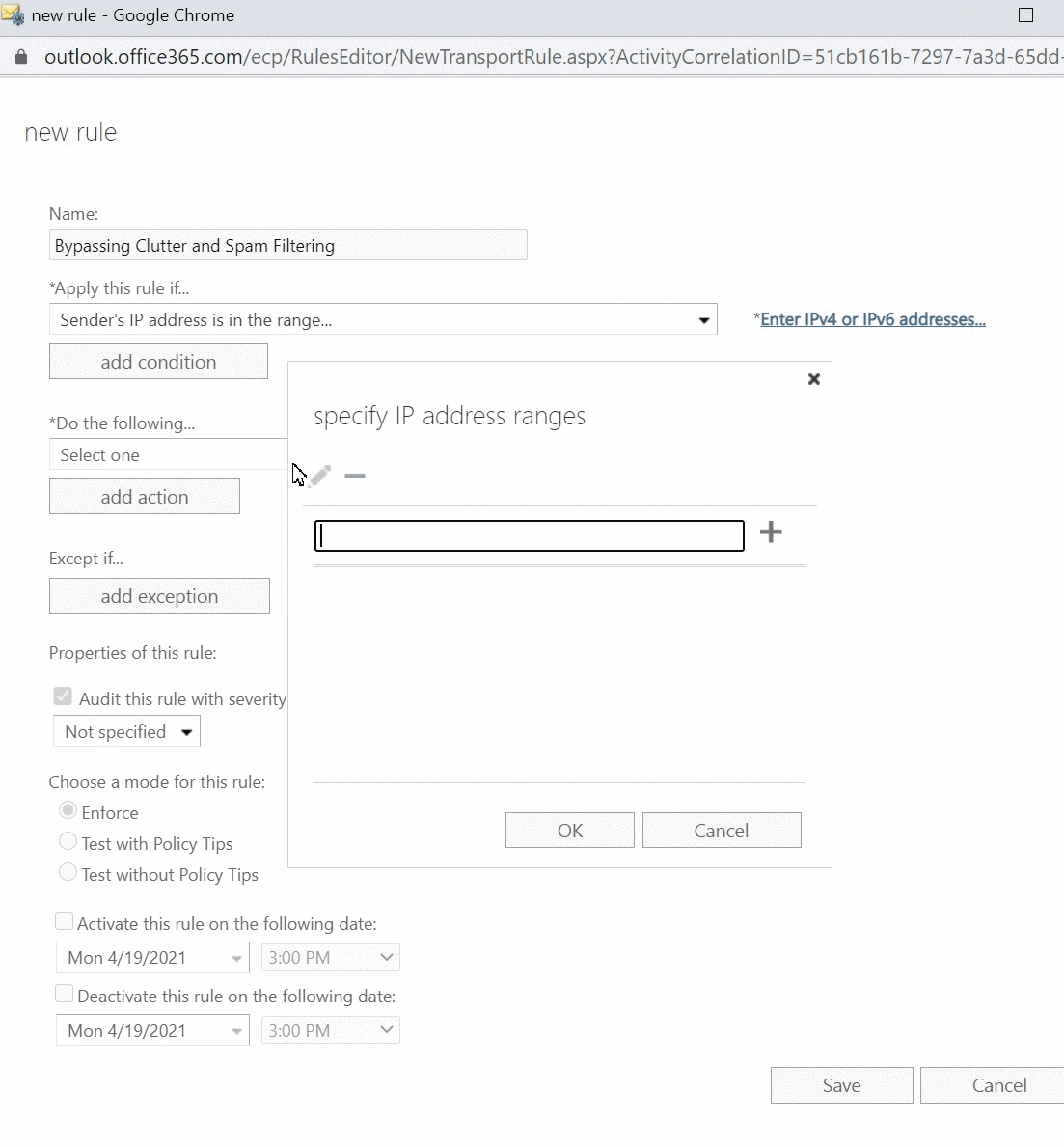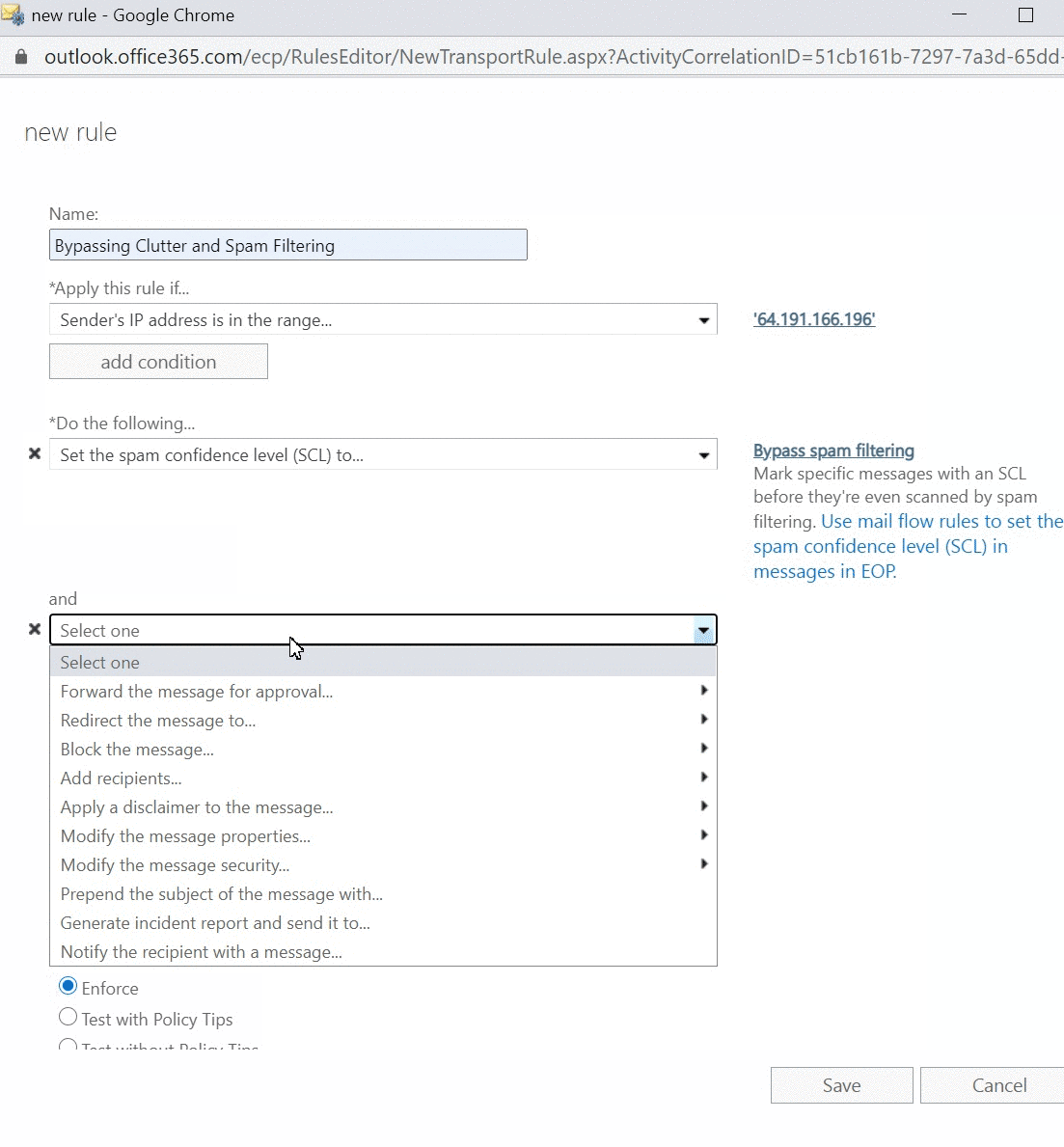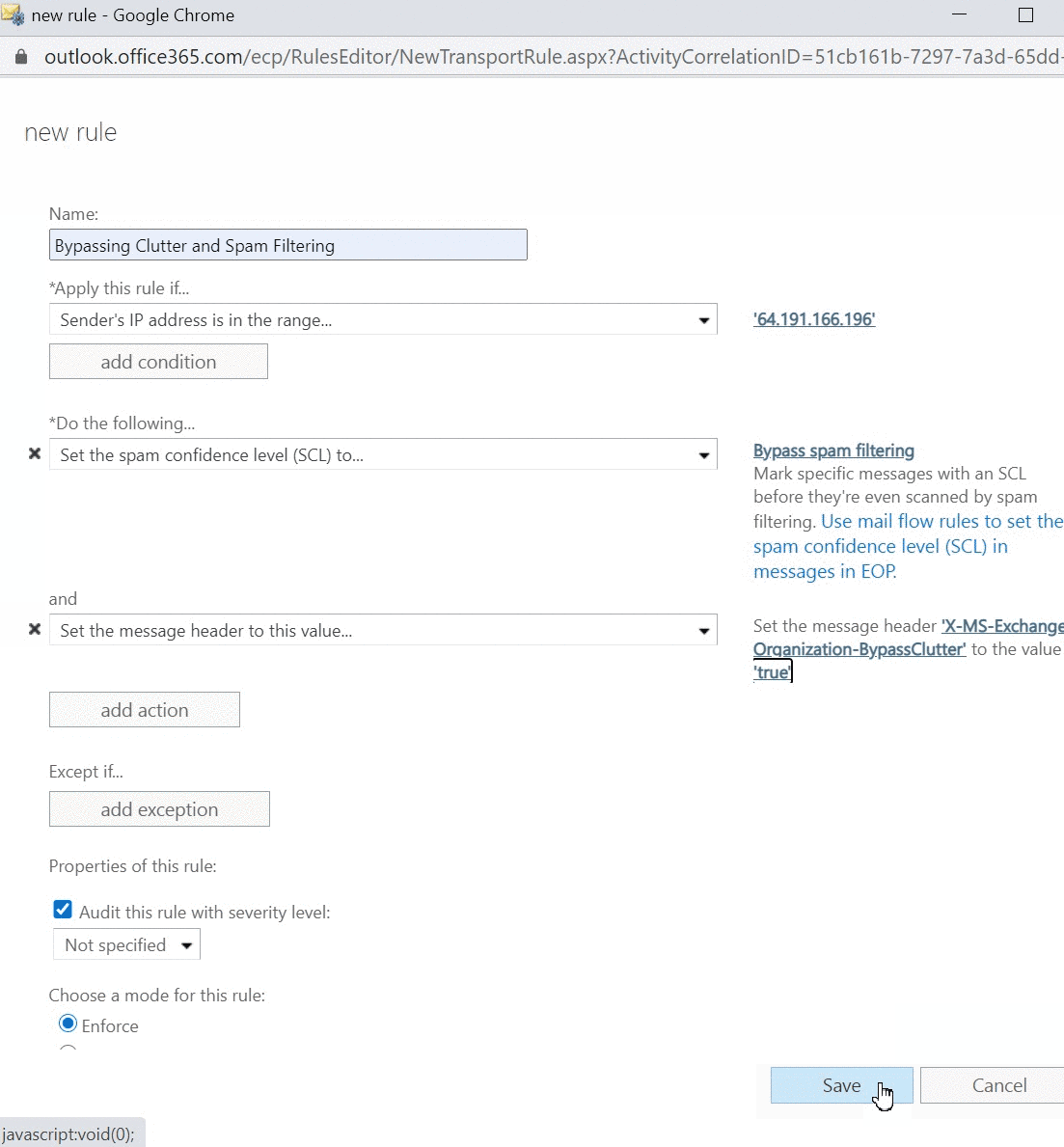
 dropdown under the Rules tab. Select Create a new rule.
dropdown under the Rules tab. Select Create a new rule. - Give the rule a name, e.g. "Bypass Clutter and Spam Filtering by IP"
- Click More options
- Add the condition Apply this rule if....
- Select The sender and select IP address is in any of these ranges or exactly matches.
- Specify the sender IP addresses which can be found in this article, then click OK.
- Do the following…
- Add a second action to Do the following... to Modify the message properties > Set a message header to this value ‘X-MS-Exchange-Organization-BypassClutter’ then click Enter text... and set to ‘true’
- Add an additional action under Do the following to Modify the message properties. Here, click on Set the spam confidence level (SCL) to... and select Bypass Spam Filtering.
- Click Save.
-
Bypassing the Junk Folder
Setting this rule will permit only simulated phishing emails from Portal to bypass the Junk folder to ensure users are receiving the simulated phishing emails in their inboxes.
Note for Office 365 Environments: If you safelisted our email servers prior to February 2018, you must add an additional mail flow rule in your Office 365 Admin center. This rule can be found below.
- Click the
 dropdown under the Rules tab. Select Create a new rule.
dropdown under the Rules tab. Select Create a new rule. - Give the rule a name, e.g. "Bypass Junk by IP"
- Click More options
- Add the condition Apply this rule if....
- Select The sender and select IP address is in any of these ranges or exactly matches.
- Specify the sender IP addresses which can be found in this article, then click OK.
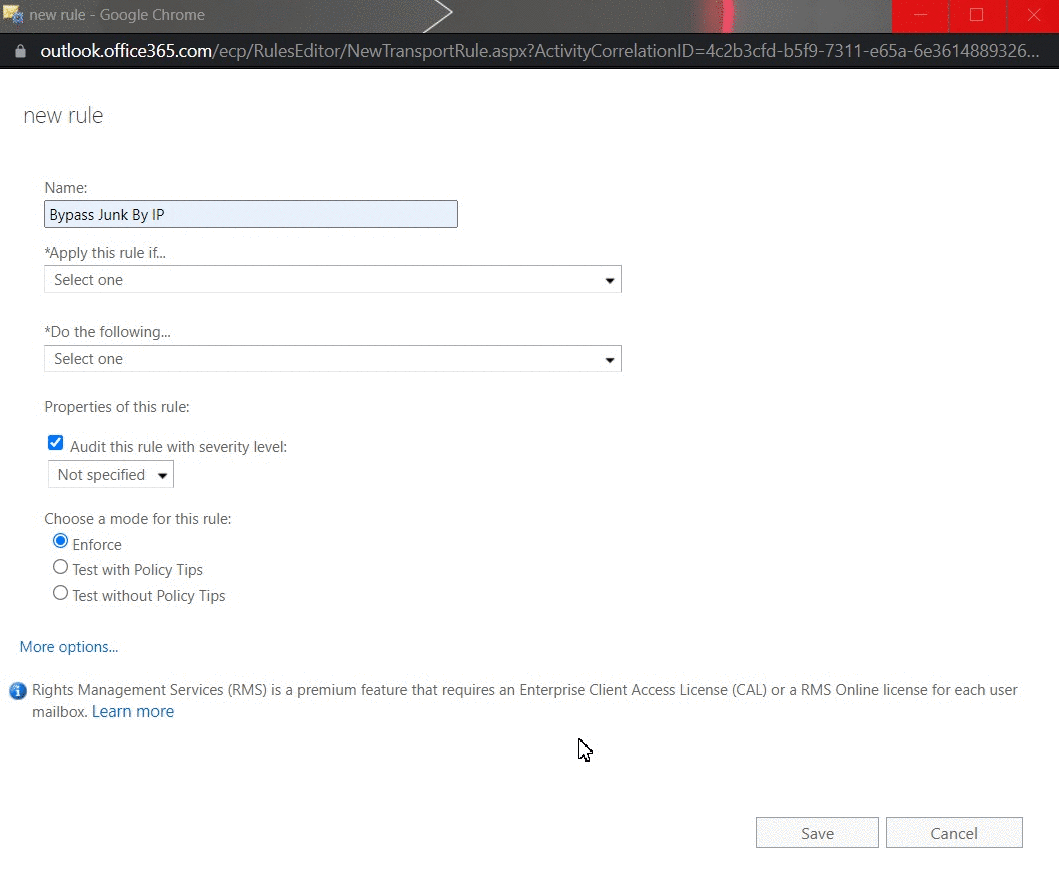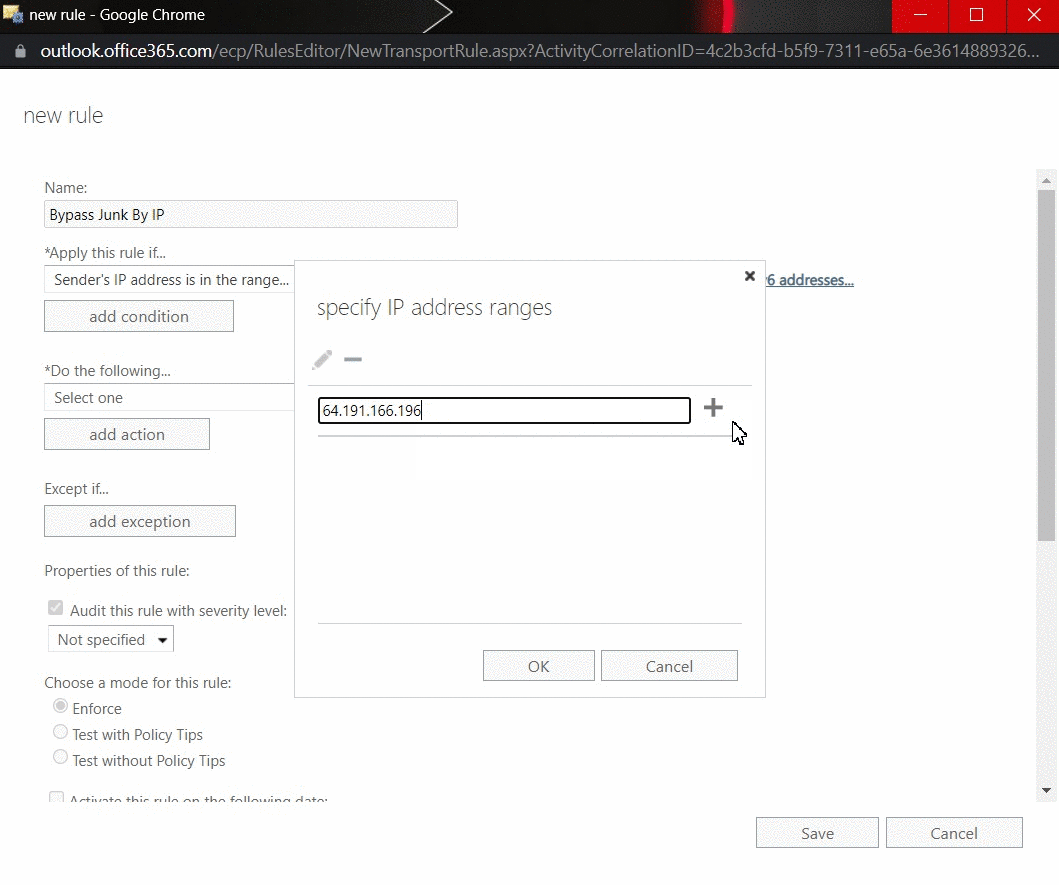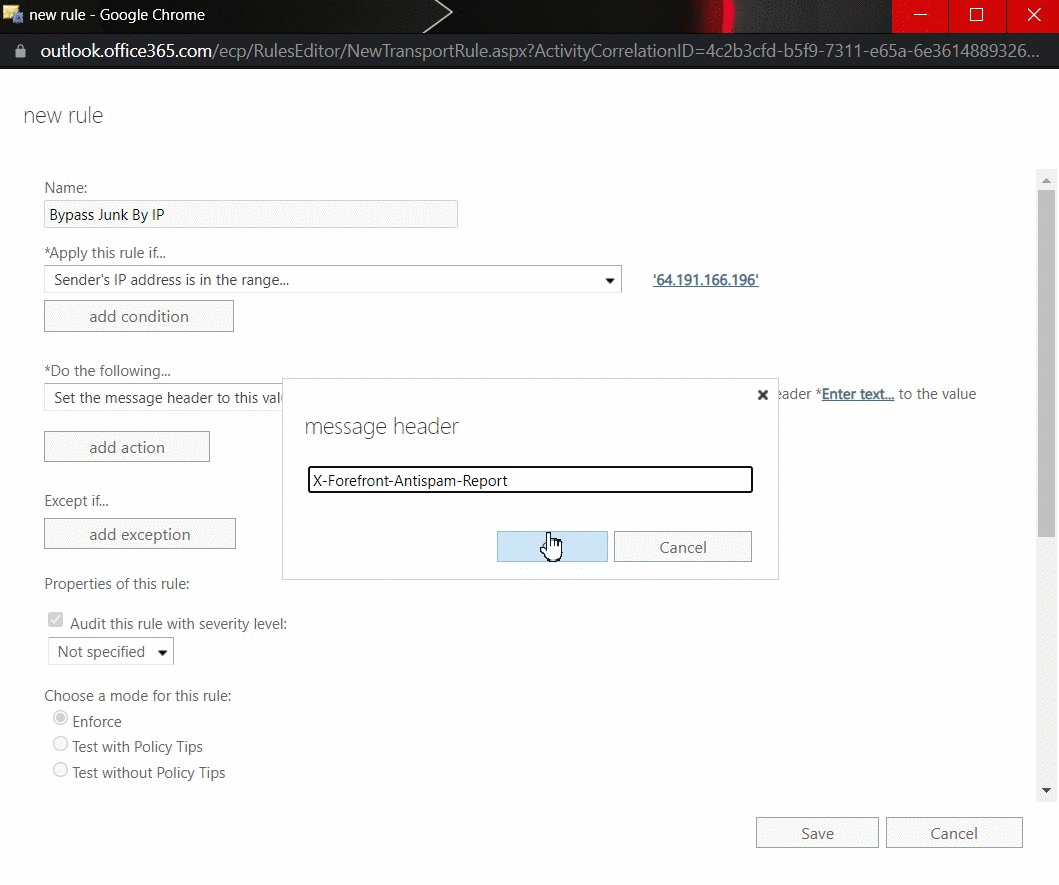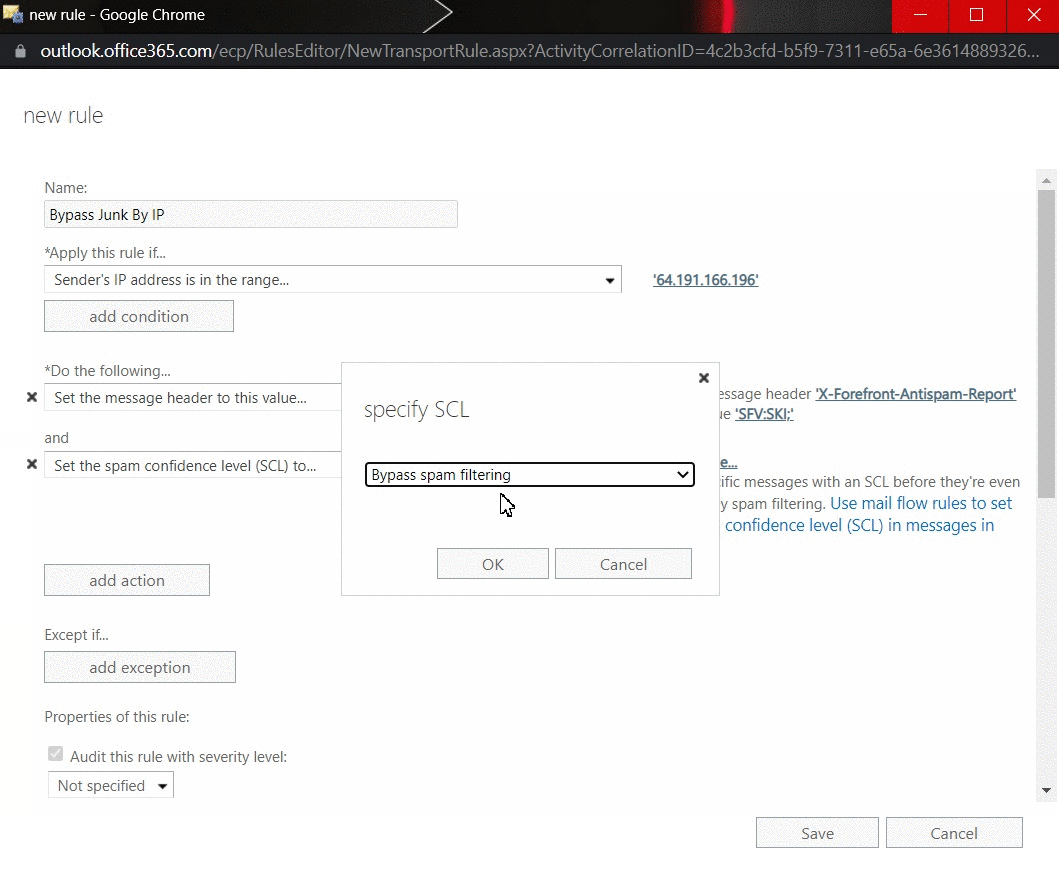
- Under Do the following, click Modify the message properties the Set a Message Header.
- Set the message header to this value: the header "X-Forefront-Antispam-Report" to the value "SFV:SKI;".
- Note: see this article to learn more about this header.
- Under Properties of this rule set the priority to directly follow the existing rule (see Bypassing Clutter and Spam Filtering) set up for Portal safelisting.
- Click Save.
-
After following the instructions above, you will want to safelist by email header as well.
After completing the steps above, we recommend that you set up a small test phishing campaign to ensure our simulated phishing emails can reach your users. If the phishing emails can reach your test inboxes, you will know you have successfully safelisted our servers.
Allow time for propagation of these rules.